What is DNSSEC?
Domain Name System Security Extensions (DNSSEC) is a set of protocols designed to enhance the security of the Domain Name System (DNS). By providing a mechanism for ensuring the integrity and authenticity of DNS data, it protects against various types of attacks, including cache poisoning and man-in-the-middle attacks. These attacks can mislead users by redirecting them to malicious websites, which can result in data theft, phishing, or other security breaches. it addresses these vulnerabilities by allowing DNS responses to be digitally signed and verified.

Table of Contents
How Does DNSSEC Work?
DNSSEC operates by leveraging cryptographic techniques that ensure the authenticity of DNS responses. Here’s a breakdown of its core components:
- Digital Signatures: Each DNS record in a zone is signed using a cryptographic algorithm, producing a digital signature known as an RRSIG (Resource Record Signature). This signature verifies that the DNS data has not been altered.
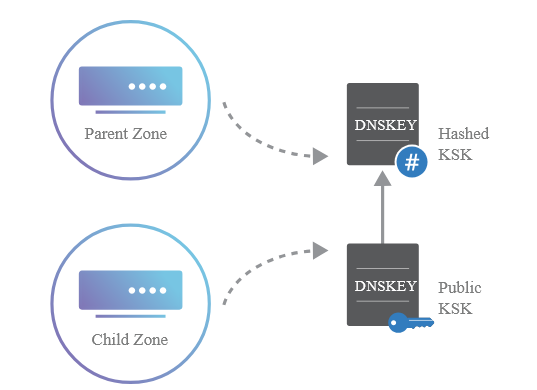
- Key Management: Employs a hierarchical key management system, which consists of two types of keys—Zone Signing Keys (ZSK) and Key Signing Keys (KSK). Each serves a specific purpose in the signing and verification process.
- Chain of Trust: Establishes a chain of trust that extends from the root DNS servers down through various levels of domains. Each zone can sign its DNS data using a ZSK, and the ZSK can be signed by a KSK, which is itself signed by the parent zone’s KSK. This hierarchical trust model ensures that resolvers can verify the authenticity of the data they receive.
Types of Signing Keys in DNSSEC
DNSSEC relies on two main types of signing keys:
- Zone Signing Key (ZSK):
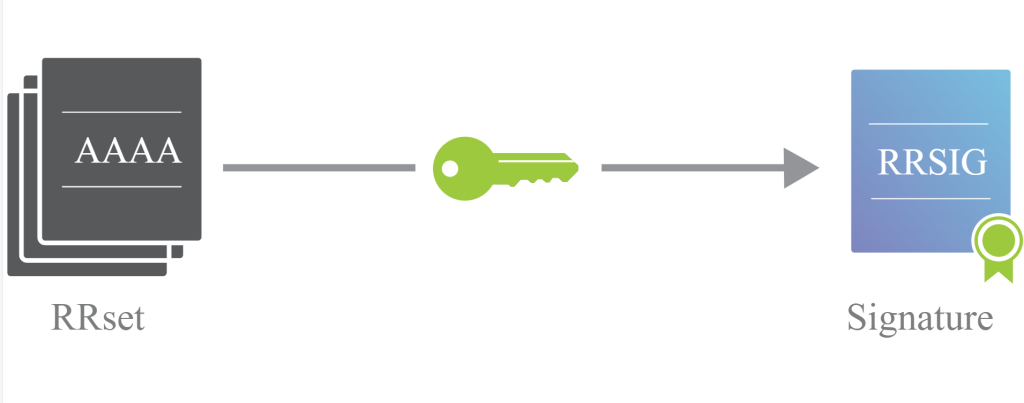
- Purpose: The ZSK is responsible for signing the DNS records within a specific zone (e.g., a domain).
- Characteristics:
- Typically shorter in length than the KSK, making it suitable for frequent use.
- Regularly rotated to minimize security risks.
- Function: When DNS records are created or updated, the ZSK signs these records, producing RRSIG records that accompany the DNS data. This ensures that the records can be verified for integrity.
- Key Signing Key (KSK):
- Purpose: The KSK is used to sign the ZSK itself, establishing a higher level of trust.
- Characteristics:
- Generally longer and more secure than the ZSK, as it is used less frequently.
- It helps maintain the chain of trust from the parent zone to the child zone.
- Function: The KSK signs the DNSKEY record set, which contains the public ZSK. This enables resolvers to trust the ZSK that signs the DNS records, ensuring that the data is authentic.
Signing and Validation Process
The signing and validation processes in DNSSEC are critical to its effectiveness:
- Signing:
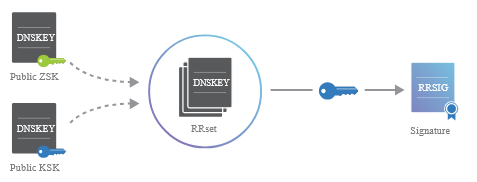
- When a zone is created or updated, its DNS records are signed with the ZSK.
- The ZSK is subsequently signed by the KSK, creating a chain of trust that links the zone to its parent domain.
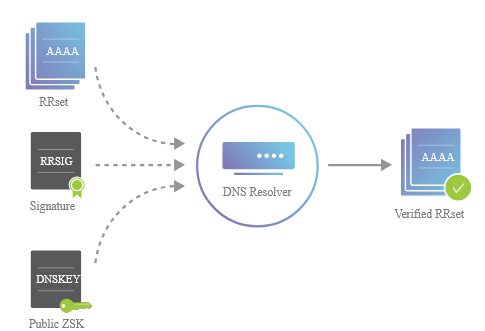
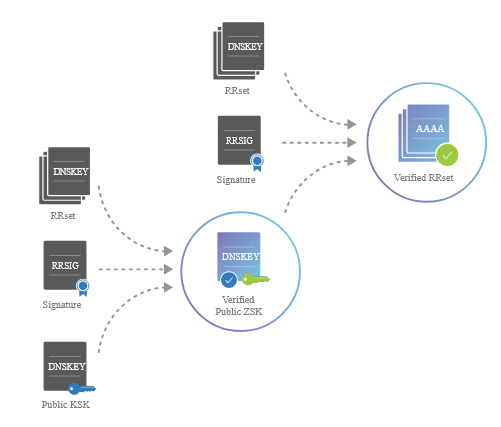
- Validation:
- When a DNS resolver queries a domain, it retrieves both the DNS records and their associated signatures (RRSIG).
- The resolver verifies the signatures using the public keys found in the DNSKEY records.
- It checks the signatures against the KSK from the parent zone, ensuring the integrity and authenticity of the data.
Advantages of DNSSEC
- Integrity: DNSSEC ensures that the data received is exactly what the authoritative source intended to send, protecting against tampering.
- Authentication: It confirms that the DNS data comes from a legitimate source, reducing the risk of attacks that can redirect users to fraudulent sites.
- Reduced Risk of Attacks: By authenticating DNS responses, DNSSEC mitigates risks associated with DNS spoofing and cache poisoning.
Challenges and Considerations
Despite its advantages, DNSSEC also presents challenges:
- Complexity: Implementing can be more complex than traditional DNS, requiring proper key management and regular updates.
- Performance: The overhead of signing and verifying DNS data may introduce slight delays in resolution times.
- Adoption: While more domains are adopting, universal implementation is still lacking, limiting its overall effectiveness.
Plays a vital role in enhancing the security of the DNS infrastructure. By using digital signatures and establishing a hierarchical chain of trust, it helps ensure the integrity and authenticity of DNS responses, thereby protecting users from various cyber threats. The use of ZSKs and KSKs in the signing process allows for robust security while requiring careful management to maintain effectiveness. As internet security concerns grow, the importance of DNSSEC will likely continue to increase.